A proxy server, or perhaps proxy for brief, is like obtaining An additional Laptop that your Web requests get sent to prior to visiting the serious website. It is a server that normally takes all of the knowledge you've got despatched out, just like a ask for to obtain new shirts on H&M, and routes it by means of a unique IP deal with.
Read further: global object
That's what tends to make a proxy so powerful. They might make all of your current World wide web exercise look as if it's coming from a very distinctive place.
Providers utilize them for protection and community effectiveness reasons, people utilize them for privacy concerns, and there's also some great operation you may faucet into when using proxy servers in your World-wide-web searching that we'll speak about later on.
A proxy could be bodily Found anywhere. You'll be able to put in place a proxy on your private home Laptop or computer or you'll be able to deploy one particular towards the cloud. The primary point that matters is that the proxy has the configurations you need for that performance you'd like.
Just take into account that a proxy functions like a elaborate IP address filter. Much like filters, you will find unique forms of proxies and they all have their particular employs.
To start out, let's talk about the most common form of proxy and how it works, the ahead proxy.
How a proxy functions
Once you listen to or see people speaking about proxies, They are more than likely referring to forward proxies. These are definitely the commonest different types of proxy because they conveniently take care of what many people want. Ahead proxies act as being the middleman in between your requests and also the server you're seeking to connect with.
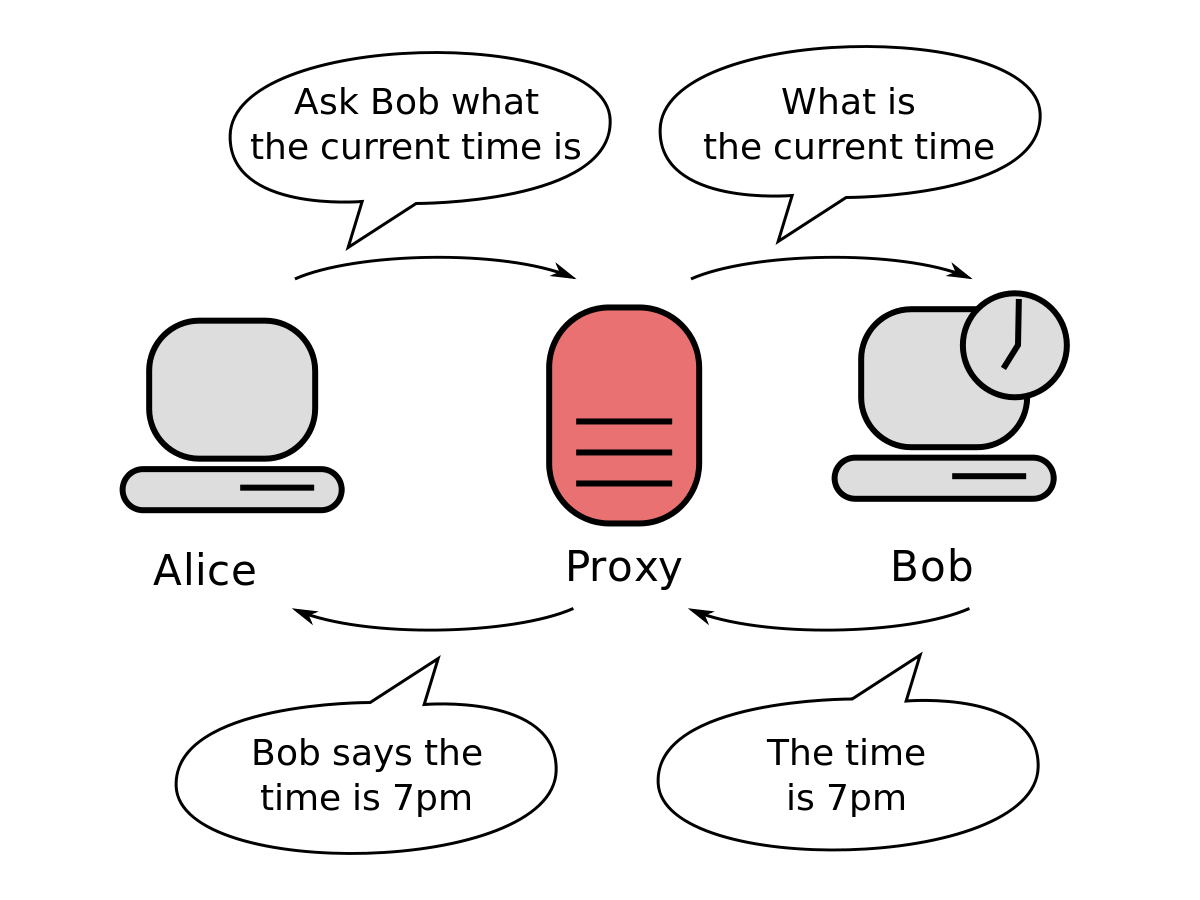
The way in which a proxy performs is to start with you create a ask for, for instance you try to go GitHub. Which means you key in the URL and strike enter. With a proxy, as opposed to connecting you directly to GitHub together with your Laptop's IP handle, your ask for gets intercepted via the proxy.
Then the proxy usually takes your request, updates it, and sends it from its own IP deal with. This could entirely remove your IP address and figuring out information in the request to the GitHub server.
On the list of ways in which proxies tackle Altering your ask for is straight inside the ask for headers it sends to the server. A proxy request can set headers like Forwarded and Via in the initial request just before it sends the concept into the server you might be endeavoring to get information and facts from.
As soon as the proxy has current the information from the ask for, it will ship your reformatted ask for on the GitHub server. That server now thinks your ask for has come from a distinct locale and it'll deliver the data you required back again through that area.
Future the proxy normally takes the data in the GitHub server and does any checks it has been configured to perform with that info. It could check for any malicious scripts or other safety issues. Then it last but not least sends the data back again in your Laptop or computer plus your webpage hundreds.
A proxy server just isn't necessarily limited to a person user at a time. There may be a number of people sending requests from the identical proxy and they might all share the exact same Rewards. There are many causes you could make use of a proxy, whether or not it's a shared just one.
Why you'd make use of a proxy
Now you know what a proxy is, It really is very good to be aware of some of the widespread use scenarios for them.
You can maximize community safety by encrypting requests
â—‹ Protect against hackers from intercepting sensitive information
â—‹ Block malware sites from the genuine community
You can reduced the amount of community targeted traffic by caching web sites
â—‹ Cache Internet sites so that just one request to the internet site is produced Regardless of how many people are over the proxy
You may control how men and women use the online world
â—‹ Block particular domains
â—‹ Observe and log all Internet requests
You can get all around blocks setup by companies and countries
â—‹ Obtain content from a distinct country
â—‹ Get around company firewalls
This is not an extensive listing of almost everything you can do with proxies, but I also preferred to incorporate a lot of the other Gains that don't really tumble underneath The everyday types.
You always have cookies blocked
You mostly have advertisements blocked
You'll be able to accessibility the deep Website
It gets rid of any lookup tailoring or monitoring your prior queries
You could scrap details
You can do exploration on your own Competitors
Differing types of Proxies
There are plenty of differing types of proxies that can go over just about any configuration that you could consider. Here, I will provide you with a brief overview of fourteen diverse proxy sorts.
Clear proxy
Clear proxies are The only style of proxy. They pass your entire information and facts alongside, but with the proxy's IP tackle. These proxies don't give virtually any privateness defense.
They tell the server you're sending your request to which the request is coming through a proxy. This is sufficient to get you all around uncomplicated IP bans. A common use for clear proxies is starting Internet site filtering, like educational institutions and corporations do.
Anonymous proxy
Anonymous proxies can be a generally applied style of proxy. They never ever pass your IP handle to the website you happen to be searching Even though they will discover by themselves like a proxy during the request. This will help keep your browsing activity private.
When you do not need focused ads pursuing you all around the web or you don't need your spot connected on your request, these are definitely some conventional proxies to use. This is usually plenty of to receive all-around most focusing on things to do, but there's still an opportunity that your information may be exposed.
Large anonymity proxy
These proxies are the most protected style because they don't go along your IP handle and private info and they do not discover on their own being a proxy when creating requests. Additionally they sporadically change the IP handle they use for requests. That is what makes it possible for superior anonymity proxies to give you the most privacy on-line.
The TOR browser works by using such a proxy. Considering that the IP address alterations sometimes, which makes it exceptionally challenging for servers to monitor what targeted traffic belongs to what consumer. If you don't want to get tracked, this is the best choice.
Distorting proxy
A distorting proxy performs equally to an anonymous proxy except it passes an IP that is certainly purposely false. It identifies by itself being a proxy and utilizes that Wrong IP handle in requests. This is excellent when you need to look as when you ended up in unique area.
This is beneficial when you want to have all around precise written content constraints. It can be like you get to pick the IP tackle you would like the proxy to make use of.
Residential proxy
Household proxies are proxies that use serious IP addresses. That means They can be the addresses of true pcs. They are the most beneficial sorts of proxies to use mainly because they appear to be normal shoppers to servers.
Any of the proxy sorts mentioned up to now can be quite a residential proxy. So long as the proxy's IP tackle is related to a Actual physical system, most of these proxies are generally undetectable and so they get about many of the geographic challenges other proxy sorts have.
Details center proxy
These are generally style of the other of household proxies. Facts Centre proxies have computer created IP addresses that are not connected to a real unit. It is like having a proxy within the cloud.
A bonus to this type of proxy is their velocity. Normally cloud support providers have extraordinary Net connections that give you speeds You could not get usually. While they would all share identical IP addresses, 1 server could host countless facts Heart proxies.
Public proxy
Of all of the proxy types, these are the most insecure, unreliable proxies obtainable. They're able to go down at any moment and several are create by hackers to steal info. The only real explanation individuals however utilize them is mainly because they are cost-free.
Although it's not hard to obtain lists of cost-free general public proxies, It's a problem to uncover great types. You hardly ever know who these proxies are hosted by and it's a big gamble to send any within your sensitive information and facts by means of just one. Any range of customers could be on the community proxy Anytime and there's not one person regulating who utilizes it.
Personal proxy
Non-public proxies have some ambiguity around the things they are because they're defined from the provider giving the provider. This might indicate your proxy can only be used by a single consumer at a time or that the proxy desires authentication before You may use it. They are like more responsible versions of general public proxies.
A non-public proxy may be clear or have substantial anonymity, comparable to a lot of the Many others earlier mentioned such as household or info Centre proxy. This proxy variety has much more to carry out with who can connect with it than the way it handles your requests.
Dedicated proxy
A devoted proxy is like a certain kind of personal proxy. It just means that the proxy can't be shared by many customers simultaneously. So just one client can connect and deliver requests.
This allows stop the IP tackle of your proxy from finding banned by distinctive Internet sites and expert services. It is one of many ways that a proxy supplier can Manage who may have entry to the proxy to ensure that it isn't staying abused.
Shared proxy
These are generally a few of The most affordable proxies available they usually get the job done just like shared servers. Clientele pool collectively and split the cost of the proxy and they could all access it concurrently. Shared proxies have a far more elaborate architecture since they manage lots of requests concurrently.
According to how sources are allotted to the shared proxy, requests may very well be slower than around your own IP tackle. Since it's dealing with numerous requests from multiple buyers, the configurations of a lot of these proxies is more critical in comparison to the Some others.
Rotating proxy
Rotating proxies do the job just a little differently with the Other individuals. Every time a consumer connects to your proxy, a whole new IP address is made for it. So they under no circumstances use the identical IP tackle over the moment.
Each and every time a consumer sends a ask for a completely new IP handle is generated. That is how proxies like the TOR browser perform to keep your anonymity. A rotating proxy presents a superior level of security and privateness when coupled with a lot of the other styles.
SSL proxy
These proxies follow the identical protocol as HTTPS requests. The 'S' in HTTPS implies SSL meaning your Net requests are safe in between your consumer as well as the server you are seeking to reach.
Which means you will get a lot more stability because your whole requests in the proxy are encrypted. Most proxies must be making use of this by default, but there's nevertheless an opportunity you'll run into some that use HTTP.
Reverse proxy
Reverse proxies are absolutely distinct from every thing we've included up to now. A reverse proxy hides the IP handle of a server you're endeavoring to ship a request to. When a server wants protection and privateness from shoppers, that's when most of these proxies are available.
These proxies are great if you might want to check entry to a server for good reasons like preserving clientele from acquiring unmonitored usage of a database. It also can aid decreased visitors on the community by passing on cached information as an alternative to producing a query every time.
Proxy Companies
In case you've accomplished a quick hunt for proxy expert services, you may realize that There are plenty from which to choose. Not all of them are created equally, so it is vital which you understand what attributes you would like from the proxy services.
A large number of services supply combos with the proxy kinds. One example is, you can discover residential, superior anonymity, SSL proxies rolled into one support. There are a few that stand out in the Some others so here's a list of them, but be sure to investigate them to determine when they meet your requirements.
https://smartproxy.com/
https://www.megaproxy.com/
https://whoer.net/webproxy
https://www.proxysite.com/
https://hide.me/en/proxy
https://www.kproxy.com/
https://www.vpnbook.com/webproxy
Proxy server vs VPN
For anyone who is informed about VPNs (Digital private networks), then you could be pondering how a proxy differs. The leading distinction is usually that a VPN secures all of your community website traffic wherever proxies only safe your World wide web targeted traffic.
Some things that VPNs safe that proxies don’t contain FTP uploads or downloads and track record operating process procedures, like updates.
The only thing proxies and VPNs have in common is that they make your internet targeted visitors appear like It really is coming from a different IP handle. That may be all they've in typical. How they deal with this is wildly unique as a result of the things they're employed for.
A proxy just passes together your internet requests, acting similar to a middleman. A VPN On the flip side tunnels your whole community activity down to the operating system degree. Proxies are usually utilized by an individual software similar to a browser or torrenting customer.
Providers usually use VPNs to Enable employees obtain company methods devoid of worrying with regard to the traffic getting intercepted or recorded by an ISP (Web provider company). These are frequently hosted over a physical Laptop or computer someplace on premises.
The great thing about VPNs is they conceal all the things you need to do. When your ISP had been to get a background of one's use, it could only see that you simply were connected to a VPN. Practically nothing regarding your targeted visitors might be witnessed. Whenever you hook up with community Wi-Fi, a VPN is the most secure preference.
With all of the advantages that come with utilizing a VPN, there are still great good reasons people today choose proxies. To begin with, VPNs are generally dearer than a proxy. You furthermore mght want first rate Pc hardware to run a VPN. The link will likely be slower than a proxy would be.
There are numerous moments once you don’t always want the kind of security that a VPN offers. If you just wish to mask your pursuits on one software in a cheap, a proxy is likely to be worthy of contemplating.
Rewards and risks
Since you know every little thing about proxies, This is an index of several of the advantages and risks connected with employing them.
Added benefits
Protected and private Net browsing
Ability to get about geo-spot restrictions
Improved network overall performance
Capacity to Manage what Web-sites customers have use of
Several types to pick from to accommodate more info particular requirements
Hazards
Your requests could return actually slow
Not all proxies encrypt your requests so your info could however leak out
No cost or affordable proxies may very well be arrange by hackers or government organizations
Proxies can disappear at any time
All of your requests and knowledge constantly undergo a third party which could be run by any person
You can find lots more Added benefits and pitfalls to employing any in the proxy server styles. This is exactly why it can be crucial to only connect with proxy servers you trust. While you are connected to a trustworthy proxy, the challenges should have been taken into account in the configurations so you may have much less to worry about.
Ways to create a straightforward proxy server
Producing your own private non-public proxy sounds a whole lot more challenging than it is actually. You can make a proxy with a pc in your home that's just as secure as most proxies You should purchase. It just will take some persistence and just a little curiosity.
Over a Linux server, you could set up Squid and set the configurations for the proxy you need to generate. You'll be able to do such things as block precise websites or need authentication before a shopper can connect with the proxy.
Here's an excellent wander by way of on creating a Squid proxy on Linux: https://devopscube.com/setup-and-configure-proxy-server/
On Windows and Mac, you have the choice of making a proxy server applying Python along with the Google Application Motor. You will need to pay for the Google Application Motor support, However they allow it to be quite reasonably priced.
Establishing a proxy such as this is a bit more involved than on Linux, but Here is a great stroll by: https://www.hongkiat.com/blog/proxy-with-google-app-engine/
How to connect to an current proxy
Connecting to proxies will likely be a simple procedure at the time you realize your proxy's data, like its IP handle and port quantity. No matter what functioning system you utilize, proxies are often swift to build.
Ordinarily you may go into your network configurations and obtain where you can enter your proxy info. Then you have to be equipped to connect and a Online page may well show up if you will find an authentication phase involved by the proxy. This is what it appears like on Home windows and Ubuntu.